Nokia IP265 Support Question
Find answers below for this question about Nokia IP265 - Security Appliance.Need a Nokia IP265 manual? We have 1 online manual for this item!
Question posted by jr on July 4th, 2011
Exporting Configuration.
Dear,
I would like to export into a readable file the complete configuration of our Nokia IP265 before replacing.
How to do that ?
Regards,
Current Answers
There are currently no answers that have been posted for this question.
Be the first to post an answer! Remember that you can earn up to 1,100 points for every answer you submit. The better the quality of your answer, the better chance it has to be accepted.
Be the first to post an answer! Remember that you can earn up to 1,100 points for every answer you submit. The better the quality of your answer, the better chance it has to be accepted.
Related Nokia IP265 Manual Pages
Security Guide - Page 1


Nokia VPN Appliance
FIPS 140-2 Cryptographic Module Security Policy
Level 2 Validation Version 1.7
Aug 2007
Module Hardware Versions: IP260, IP265, IP1220, and IP1260
Firmware Versions: IPSO v3.9 and v4.1 Check Point VPN-1 NGX (R60) [HFA-03]
© Copyright 2005, 2006, 2007 Nokia
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
Security Guide - Page 2


...41
APPENDIX B - Table of Contents
1 INTRODUCTION...3
1.1 PURPOSE...3 1.2 REFERENCES ...3
2 NOKIA VPN APPLIANCE 4
2.1 OVERVIEW ...4 2.2 CRYPTOGRAPHIC MODULE 5 2.3 MODULE INTERFACES 7 2.4 ROLES AND ...2.9 SELF-TESTS...24 2.10 DESIGN ASSURANCE 25 2.11 MITIGATION OF OTHER ATTACKS 25
3 SECURE OPERATION (APPROVED MODE 26
3.1 CRYPTO OFFICER GUIDANCE 26 3.1.1 Hardware Setup 26 3.1.2 Installing...
Security Guide - Page 3


... operation. Additional information regarding the Check Point VPN-1 firmware that require retesting under FIPS 140-2 (FIPS 140-2 Certificate numbers 450 and 834). 1 INTRODUCTION
1.1 Purpose
This document is used inside the Nokia VPN Appliances, including specific configuration instructions for the firmware can be found by referencing the Check Point VPN-1 FIPS 140-2 security policy, available at...
Security Guide - Page 4


... IP260 IP265 IP1220 IP1260
CPU Type Celeron Celeron Xeon Xeon
Firewall Speed 272Mbps 272Mbps 2.2Gbps 3.9Gbps
VPN Speed (AES, TDES) 113Mbps 113Mbps 1.2Gbps 1.7Gbps
© Copyright 2005, 2006, 2007 Nokia Page 4 of IP-routing functions and protocols, including RIPv1/RIPv2, IGRP, OSPF and BGP4 for unicast traffic and DVMRP for networks. As network devices, the Nokia VPN Appliances...
Security Guide - Page 5


... the complete Nokia VPN Appliance FIPS 140-2 solution. All component slots are performed by both Check Point and Nokia. The following hardware versions:
ƒ IP260 / IP265 - FIPS Algorithm validation testing was retested as multi-chip standalone cryptographic modules. full width 2U rack mount
The IP1220 and IP1260 hardware chasses include support for VPN and firewall functionalities...
Security Guide - Page 8


...network ports...firewall, VPN, and routing functionalities of the modules.
• Control input consists of manual control inputs for power and reset through the LEDs and the status data that use the CLI to configure... and monitor IPSO systems. This can be done locally by using the console port or remotely by using the SSH secured management session.
© Copyright 2005, 2006, 2007 Nokia...
Security Guide - Page 9


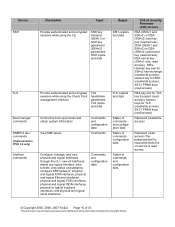
..., Descriptions, Inputs, and Outputs
Description
Input
Output
Provide network connectivity and set a password for the admin account
Commands and configuration data(via local console)
Status of commands and configuration data
Critical Security Parameter (CSP) Access
Admin password (read/write access)
© Copyright 2005, 2006, 2007 Nokia Page 9 of the Check Point module through the CLI...
Security Guide - Page 10

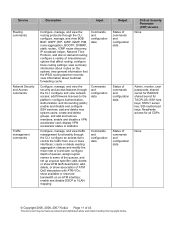
... access)
Password (read access) The password itself is read-write while the v3 service is read access
© Copyright 2005, 2006, 2007 Nokia Page 10 of commands and configuration data
Critical Security Parameter (CSP) Access
RSA (SSHv1 and SSHv2) or DSA (SSHv2) host key pair (read access) ;RSA (SSHv1 and SSHv2) or DSA...
Security Guide - Page 11

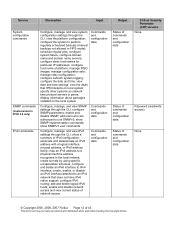
... summary information about multicast forwarding cache
Commands and configuration data
Configure, manage, and view the security and access features through the CLI: configure and view network access; shared secret for all CSPs
None
© Copyright 2005, 2006, 2007 Nokia Page 11 of commands and configuration data
Critical Security Parameter (CSP) Access None
Admin, monitor, user passwords...
Security Guide - Page 12

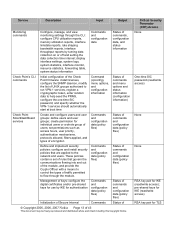
... and view current status of network access
Commands and configuration data
Output
Status of commands and configuration data
Status of commands and configuration data
Status of commands and configuration data
Critical Security Parameter (CSP) Access None
Password (read/write access) None
© Copyright 2005, 2006, 2007 Nokia Page 12 of IPv6 configuration; configure static host names for...
Security Guide - Page 13

... set of rules that are applied to the network and users. pre-shared keys for IKE (read /write access); Critical Security Parameter (CSP) Access None
One-time SIC password...authentication
Commands and configuration data (policy files)
Status of commands and configuration data (policy files)
Initialization of Secure Internal
Commands Status of
© Copyright 2005, 2006, 2007 Nokia Page 13 ...
Security Guide - Page 14
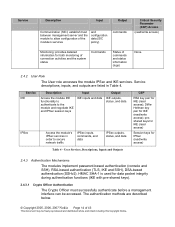

...allow configuration of the module's services
and configuration data (SIC policy)
commands
Critical Security Parameter...): establish trust between management server and the module to secure network traffic
IPSec inputs, commands, and data
IPSec outputs,...and outputs are described below.
© Copyright 2005, 2006, 2007 Nokia Page 14 of commands and status information (logs)
None
2.4.2 User...
Security Guide - Page 16
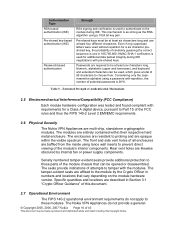

...for a Class A digital device, pursuant to Part 15 of Authentication Mechanisms
2.5 Electromechanical Interference/Compatibility (FCC Compliance)
Each module hardware configuration was tested and found ... and thus the FIPS 140-2 Level 2 EMI/EMC requirements.
2.6 Physical Security
The Nokia VPN Appliances are opaque within their respective hard metal enclosure. The enclosures are resistant to...
Security Guide - Page 20


... a FIPS-approved mode of operation:
Session security:
• SSHv1 (configured to use FIPS-approved algorithms)
• SSHv2 (configured to use FIPS-approved algorithms)
• TLS v1.0 (configured to use FIPS-approved algorithms) according to RFC 2246
• IPSec (configured to use FIPS-approved algorithms) © Copyright 2005, 2006, 2007 Nokia Page 20 of encryption strength. Pseudo...
Security Guide - Page 25


... the policy files are logged and produce error indicators.
2.10 Design Assurance Nokia and Check Point manage and record their respective source code and associated documentation files. Nokia implements the... logging.
2.11 Mitigation of Other Attacks The modules do not employ security mechanisms to provide configuration management for the module's FIPS documentation. If the IPSO kernel modules...
Security Guide - Page 26


...Within the carton the module is complete.
two foam end caps are in...secure operation procedures include the initial setup, configuring the Check Point modules in a FIPS compliant manner, and keeping the module in determining whether the original labels have been replaced. The secure...in the packaging. 3 SECURE OPERATION (APPROVED MODE)
The Nokia VPN Appliances meet Level 2 requirements for...
Security Guide - Page 27


...screws on whether or not Flash cards are installed.
3. Refer to
completely cure. Tamper Seal Location for the Nokia VPN appliances. Allow 24 hours for the adhesive in the tamper-evident seal(s) ...seals over the Flash memory bays when configuring the module in the figures below.
2.
Tamper Seal Locations for placement of the module as shown in a security log. 4. Figure 2 - For the...
Security Guide - Page 29


...7. Delete Check Point VPN-1 version R55p:
1. Access the device via Voyager, the web-based management interface, Click on the...file from the home page follow the instructions below to install the NGX with Check Point VPN-1 version R55p running a FIPS 140-2 validated configuration... Point VPN-1 Pro/Express R55p
3. For older Nokia VPN Appliance modules, the Crypto Officer may need to upgrade the...
Security Guide - Page 31


...device that the Crypto Officer establishes the SIC configuration. This is running 3.7.99 FIPS build with -restore' command followed by the 'save config' command. Groups 15-18 (3072 bits to initialize secure... and (C) above , follow the instructions.
You will be configured.
© Copyright 2005, 2006, 2007 Nokia Page 31 of the module.
Using the SmartDashboard application, the...
Security Guide - Page 33


... SSHv2, or both with SSH-secured management sessions. When changing the configuration, the preceding settings denoted by ...2006, 2007 Nokia Page 33 of the module function. Enter the Crypto Officer's authorized public key for encryption and configure the SSH ... not included in IPSO v4.1). These policies determine how the firewall and VPN services of 43
This document may be freely reproduced...
Similar Questions
Which Phone (no Touch Screen)is The Same With My Old Nokia 6120 Classic?
(Posted by roulanatsoudi 8 years ago)
How Do You Check Memory On Checkpoint Ip390 Appliance
(Posted by awkhjohn 9 years ago)
I Can See My Video When Connected To Pc But Can't See On Mobile. Why So?
(Posted by Anonymous-98944 11 years ago)
I Am Using Nokia 6700 , From Past 2 Days M Not Having Network In My Cell ...
(Posted by humafatima46 12 years ago)

